In the previous chapter we briefly discussed social networks, social engineering, and various types of social engineering attacks. This chapter will dive deeper into the most common form of social engineering, Phishing. We will discuss what phishing is, how it’s carried out, and what red flags to look for when opening an email.
Many have heard of phishing emails but what exactly are they? A phishing email is an email that is sent to a target containing fraudulent links, images, attachments, or information in hopes of receiving valuable resources such as money or data. Phishers attempt to trick their victim into acting quickly and making mistakes. There is also a variant of Phishing known as Spear Phishing. Spear Phishers have the same goal in mind but typically send more realistic and personal emails posing as a friend, co-worker, or family member. As mentioned in the previous chapter, these attackers use social networking sites to gather personal information which makes for a more believable spear phishing attempt.
Common Red Flags
Deceiving Email Address:
- Upon receiving an email, one of the first things you should do is review the email address. Cyber criminals will often try to mimic the email address of a trusted person or organization. For example: bobcyber@aerospace.org is an entirely different email address than bobcyber@aerospace.com. Small things like this are some of the first red flags to look for.
Generic Greeting:
- If an email appears to be from a legitimate organization, it would be safe to assume that they would address you by name. A legitimate email will not address you as “Co-worker” or “Valued Customer”. This is generally another strong sign that it is a fraudulent email.
Poor Grammar:
- Another common theme in phishing emails is incorrect grammar. There could only be one or two mistakes throughout the email, but if these mistakes are present, it should definitely raise a red flag. A majority of these issues have to do with the use of singular/ plural or past/ present.
Sense of Urgency:
- Phishers try to create a sense of urgency so you’ll click on their attachment or link quickly. This is done to test the emotional intelligence of the users and tempt them to click before they get a chance to think rationally.
Deceptive URL/ Hyperlink:
- When a link is sent in an email, always hover over it with your mouse pointer to make sure that they match up. For example: try hovering over www.google.com, you can see that at first glance it appears to be a link to Google but when you hover over the link with your cursor, you can see, in the bottom left hand of your screen, that the link is actually directing to Yahoo. While this example causes no real harm, it shows easy it can be to send someone to a malicious site.
Lack of Contact Information:
- This is another key identifier of a malicious email – the sender will not provide any contact information. Most legitimate senders will have an email signature containing their name and contact information.
Basic Components of a URL
Understanding the various segments of a Uniform Resource Locator (URL) is very important when determining its legitimacy. Each website will have a unique URL as well as the various pages on said website. Let’s take a look at the URL of this page and break it down into pieces.
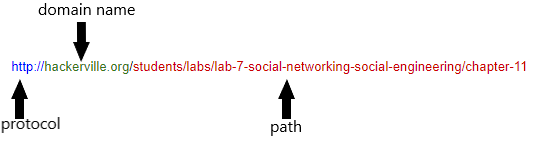
Protocol:
The protocol is the first element of a URL. In the example above, the protocol is http. The protocol is used by the web browser to determine how it should communicate with the web server. HTTP or HyperText Transfer Protocol is just one of many protocols used to define how data and messages are formatted and transmitted.
Domain Name:
The next element of the URL is the websites domain name. The domain name in this example is: hackerville.org. The purpose of a domain name is to create a unique reference for a website. Cyber criminals often try to take advantage of domain names by creating malicious sites that appear to have the same domain name as a legitimate site. For example, hackerville.org and hackerville.ru.org are two totally separate domains and websites.
Path
The path of a URL refers to the chain of folders in which the page is housed on the web server. In our example, the path is:
/students/labs/lab-7-social-networking-social-engineering/chapter-11-social-engineering-phishing-for-suckers/
In between each forward slash ‘/’ you can see the various page names leading up to this one (the page that you are currently on).
Now that you have been trained to spot phishing emails and dissect URLs, see if you can give Bob Cyber a hand in determining the legitimacy of his emails on the next page.
References:
[1] Beal, Vangie. “Domain Name.” Domain Name – Webopedia Definition, 2020, www.webopedia.com/TERM/D/domain_name.html.
[2] Chi, Clifford. “The Parts of a URL: A Short & Sweet Guide.” HubSpot Blog, 25 Sept. 2018, blog.hubspot.com/marketing/parts-url.
[3] “Anatomy of a URL.” Web Design Links, 6 Mar. 2010, doepud.co.uk/blog/anatomy-of-a-url.