As covered in chapter 1, the internet service provider (ISP) physically connects their infrastructure to the internet backbone – the information superhighway stretching across continents. The ISP’s infrastructure is then extended to homes using fiber optics, cable, dsl, or satellite and left open for a connection with a modem. If a home only ever had a single device needing the internet then connecting a wire from the device to the modem would be all the setup necessary. That device, through the modem, through the ISP, would be connected to the internet backbone same as any destination to which it could want to communicate with. Nowadays, a single device in the home needing the internet is simply not the case. Not only are more devices than ever needing to connect to the internet, but not all of them, like smart phones, would be comfortable with a wired connection. Therefore, another piece of hardware is necessary to facilitate wireless connections and multiple devices sharing the same internet connection. This device is known as a router.
The router becomes this one device in the home with a wired connection to the modem and all other devices wanting an internet connection must associate/go-through the router. The router, in its privileged position as the gateway for all devices in the home to the internet, has acquired numerous other responsibilities. The term “router” only refers to its role ensuring different devices can share the same physical wire and that data does not mistakenly end up at the wrong device. Other roles include: acting as the nearest DNS server and the DHCP server to perform the functions discussed in chapter 2, acting as an access point to enable wireless connections, acting as a switch to enable wired connections, and acting as a firewall to provide security.

Connecting a device to the router can happen one of two ways: wired or wirelessly. Through Ethernet or through Wireless Fidelity (Wi-Fi). First, we will cover connecting a device to a wireless interface on the router as it is a lot more involved before the device can successfully send information through the access point.
Every 100 milliseconds the router, acting in its role as an access point (AP), sends out wireless data called a “beacon” in all directions to announce its presence to prospective devices. That list on your device of nearby Wi-Fi networks is actually beacons your device has heard lately. It should be noted that if 100 milliseconds is too long a wait your device does have the ability to actively search for beacons by sending out its own wireless data in all directions called a “probe request.”
The beacon contains the potentially hilarious network name as well as protocols the access point supports for things like sending and protecting data. Wireless devices have a number of unique challenges not found in wired connections that the protocols need to overcome. Here are a few:
- Shared airspace. Each device is not at the end of its own, uninterrupted wire going straight to the router. All wireless devices compete with each other to get their data to the access point. If any two devices send their data at the same time it will cancel each other out and both will fail. The protocol needs to detect when failures happen and respond to prevent more from occurring.
- Power Saving Mode. Wired connections are typically stationary and as such also have a wired power connection. Wireless devices typically run on battery power so the protocol needs to keep internet services as fully functional as possible while consuming as little power as possible.
- Movement. This is more a problem for large businesses with entire buildings to cover than for smaller homes, but a wireless device may be close to an access point one minute and far away the next minute. The more distance between an access point and a device the harder it becomes to maintain reliable data transmissions. Wireless protocols need a way to detect device movement and respond accordingly.
Because of these challenges and many more, one of the first steps when a device tries to connect to a wireless network is negotiating which protocols to use. This happens in about as a complicated a manner as figuring out what restaurant to eat at. The device picks some protocols from the list found in the beacon it also supports and, if those do not work for the access point, the AP will offer a counter-suggestion. After the protocols are agreed upon, the device needs to use those protocols to authenticate with the router – another unique challenge of Wi-Fi. There’s a reason you never need to know an internet password when using a wired connection. It’s assumed if you can run a wire from the device to the router then you are supposed to be there. That isn’t the case with Wi-Fi. Before the router will let you send any messages, you need to prove this device is allowed to send messages by submitting the password. After authenticating, the device is associated with the router and given any information still needed to communicate with the internet through it. When hooking up devices with a wired connection, it starts at this step. As soon as both ends of the cord are plugged in, it is given all the required information. Transportation/security of data are inherent to the cord, so it doesn’t need to be any more complicated than that.
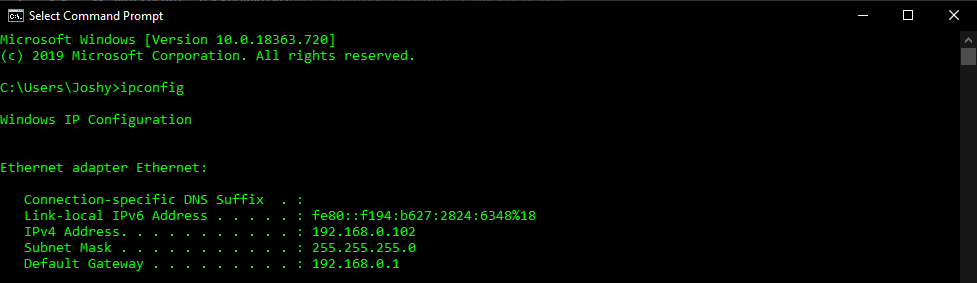
Whether connecting wired or wirelessly, the command “ipconfig”, an abbreviation of “Internet Protocol (IP) Configuration”, is useful to confirm the connected status of a device (this command is “ifconfig” on Linux devices). It contains the information established during the connection process needed to get data destined for the internet from the device to the router (chapter 3). From the router the data goes to the modem and onto our Internet Service Provider’s (ISP) network. Our ISP will send the data to the final destination if it’s also connected to our ISP or escalate it to the internet backbone if it’s not (chapter 1). The internet backbone will get the data into the right area where the data then moves onto the destination’s ISP’s network. Now, the process works in reverse. The destination’s ISP routes our data through its network to the destination’s modem. Then to the destination’s router. Then to the destination. Each of these steps, each of these nodes, utilizes IP addresses and routing tables to figure out where the data needs to go (chapter 2).

Now you know how the internet works. Numerous interconnected devices passing information between each other to move data from one end to other one small step at a time. Fundamentally, the internet is just a more organized version of using other students to pass notes between friends seated apart in class. Although in this case, the students in-between have wised up and started charging for the service of passing the note along. Now that you know how the internet works, we have one final question:
Can you recall if you’ve ever had to prove why you need to go to a particular website? Can you recall if you’ve ever been stopped along the way to Amazon.com to prove why you should even be allowed to connect to this website? Sure a website might have a login, but you’ve already connected to the website to get to that login page. You had to find where to click “log in” or be immediately confronted with it, but at that point the connection has already been made. The answer to the question is no. You’ve never had to prove why and it can be ridiculous imagining the internet if it was ever yes. How would it even go about doing that? Absolutely none of the discussed protocols: IP addresses, DHCP, DNS, routing tables, ARP – absolutely none of them ever verify if they should be carrying this data they only worry about getting it to the destination. Even the access point authentication talked about earlier won’t do this. Sure you need to input a password but after that it will still forward every data packet it receives with your IP address to your device whether this is data you want or not. This is how spam happens; how malicious links happen; how hacking attempts happen. The underlying protocols behind how the internet works never question the data they are carrying. They are only concerned about getting that data to the destination. This is also why good judgement and firewalls are so important. By default, the internet is not looking out for your best interests. It is merely a way of moving data from point A to point B. Firewalls can go a long way to stop you from ever seeing bad data, but they can never be perfect. Practice good judgement and stay safe.
If you would like to learn more about internet-related topics like the country-wide shut-off switch or other ways to deliver an internet connection than just dsl or cable, check out the bonus chapter: diversity of the internet.
Definitions:
Router: Networking device responsible for forwarding packets between networks. It has since become a catch-all term for all the functions provided by the same piece of physical hardware. Many Internet Service Providers (ISP) have recommended router versions to use with their modems.
Access Point: The part of the router responsible for wireless communications. Large areas needing reliable wireless will separate the access point into its own piece of hardware connected to the router via an ethernet wire. That way, many access points can be spread out across the area to reduce the distance a device needs to transmit.
Switch: The part of the router responsible for wired communications. Each ethernet interface on a switch is like its own tunnel. Data destined for a device at the end of one wire will not be replicated across any other wires. This is in contrast to another networking device enabling wired communications called a hub. A hub will do exactly that; replicate data across all wires. Data replication is usual for network administrators trying to monitor internet usage. A switch may split-the-difference by having just one interface available to receive duplicates of the data going to all other interfaces.
Firewall: The part of the router responsible for security. Internet Protocol (IP), the broader protocol using IP addresses, has no security built-in. Anyone can send something to anyone else. It only deals with getting data from one place to the other. Therefore, having a firewall is useful to filter out all unsolicited communications.
Ethernet: Adopted as the wired communication standard in 1983. While all ethernet cords look alike, not all are the same. Some are shielded to prevent outside interference and some sacrificed speed to transport reliably over a longer distance. The “cat”, an abbreviation of “category” standard helps to differentiate between cord variations with cat5e and cat6 being the current standards .
Wireless Fidelity (Wi-Fi): A term used for wireless communications. Unlike ethernet, Wi-Fi is not actually a protocol or a standard, just a catchy term for wireless internet. In fact, numerous different wireless protocols have been developed and all have their own strengths and weaknesses. Some are better for speed and some are better for reliability. This is why it is important that one of the first thing wireless devices do is pick a wireless protocol both support.