Social networking gained popularity shortly after the birth of the internet. In 1978, the Bulletin Board System or BBS launched. BBS allowed users to connect to a central server and perform various social networking functions such as: download software, read news articles, and message others privately or publicly. The new phenomenon of social networking allowed people to interact and connect with more people than ever humanly possible. Social networking quickly morphed into social media and captured the attention of all age groups. The image below helps to visualize how quickly companies are entering the multi-billion dollar market.
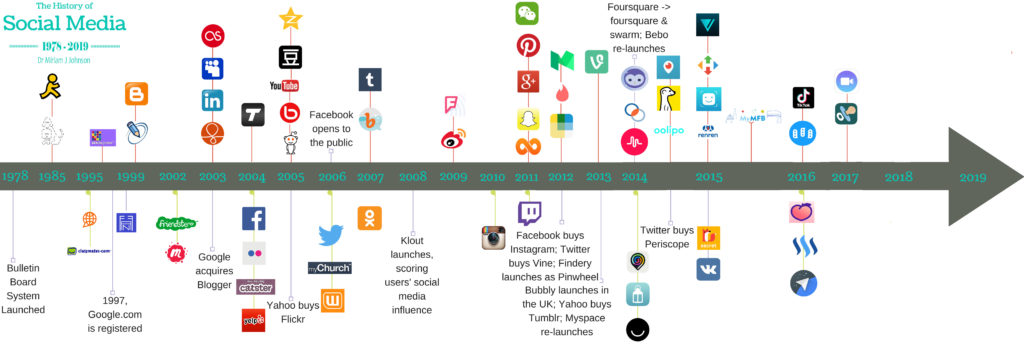
As more and more social media sites emerge, it has become essential to understand how to use these sites in a secure and responsible manner. While social networking has presented its users with limitless opportunities, those same opportunities are now being exploited by cyber criminals. Everything from Facebook to email introduces potential threats to its users. Since the number of daily users is increasing exponentially, as shown in the image below, efforts to protect our data will only need to increase and it all starts with you, the user.

Social Engineering
Before diving into social media best practices, it is important to understand how one’s actions on a social platform can come with consequences. Attackers cannot simply message or upload malware directly to your computer without any interaction from the targeted user. Cyber criminals use something called social engineering to trick their victims into falling for their trap. These criminals will attempt to collect data on their victim in order to better cater their attack. So what does this mean? Essentially a cyber criminal will first do reconnaissance to gather information that will allow them to manipulate and deceive their victim into handing over data, money, or information for fraudulent purposes. Here are a few types of social engineering:
Phishing
- Phishing is the most prevalent and successful form of social engineering. An attacker will send deceiving links or attachments to a person via email or any social media platform in hopes that the user will either click on the malicious hyperlink / attachment or divulge confidential / personal information.
Spear Phishing
- Spear Phishing is very similar to phishing but adds an additional element of personalization. For example, instead of sending a fraudulent banking request, they will send an email posing as a friend or co-worker. A user will be much less cautious when opening an attachment from someone they think they know.
Quid Pro Quo
- Quid pro quo refers to an attacker that poses as technical support. They will claim to be contacting their victim about a technical problem. A good majority of people will ignore these calls or emails but eventually, the email will land in the inbox of a person in need of technical support. Once the attacker has their victim hooked, they will often be granted full access to their target computer where they can install malware or steal information.
Baiting
- Baiting relies on the curiosity of their victim. A great example of baiting is shown in the TV show Mr. Robot. In the show, one of the hackers drops an abundance of USB flash-drives in the parking lot of a police department. One curious police officer picks one up, plugs it into his computer, and the contents of the flash-drive quickly download malware and lock the computer. The simple lesson here is to NEVER plug in foreign USB drives to your computer!
The four social engineering types, listed above, are only a few of the possible ways that cyber criminals use social engineering. In the next chapter, I will dive deeper in to how you can spot a phishing email.
What can be done?
Now that we know about a few social engineering methods, what can you do at home, school, or work to better protect yourself from these? To begin, the main similarity in any social engineering attack is the necessity for user involvement. Users need to be aware of both their surroundings, as well as their emotions. A majority of successful social engineering attacks can be avoided by simply taking a few more seconds to think about the situation. A few helpful questions to ask yourself before clicking on a link or responding to a message include:
- Is this scenario too good to be true? Chances are, you didn’t win an all inclusive cruise to Sandals Jamaica that you didn’t even apply for.
- Is this a person that I regularly contact? Does this sound like something they would ask from me?
- Does the message attempt to toy with my emotions or act urgently?
If any of these questions raise a red flag, the message or email needs to be further evaluated prior to engaging with the sender.
It is also of utmost importance to be aware of what you share on your social media platforms. The common rule of thumb is don’t post anything that you wouldn’t want your grandmother to see. Whether the post was made minutes or years ago, they could come back to haunt you when applying for jobs, schools, and more. Additionally, posting travel plans or your whereabouts can help criminals better plan their robbery attempts. A few other tips are illustrated below.
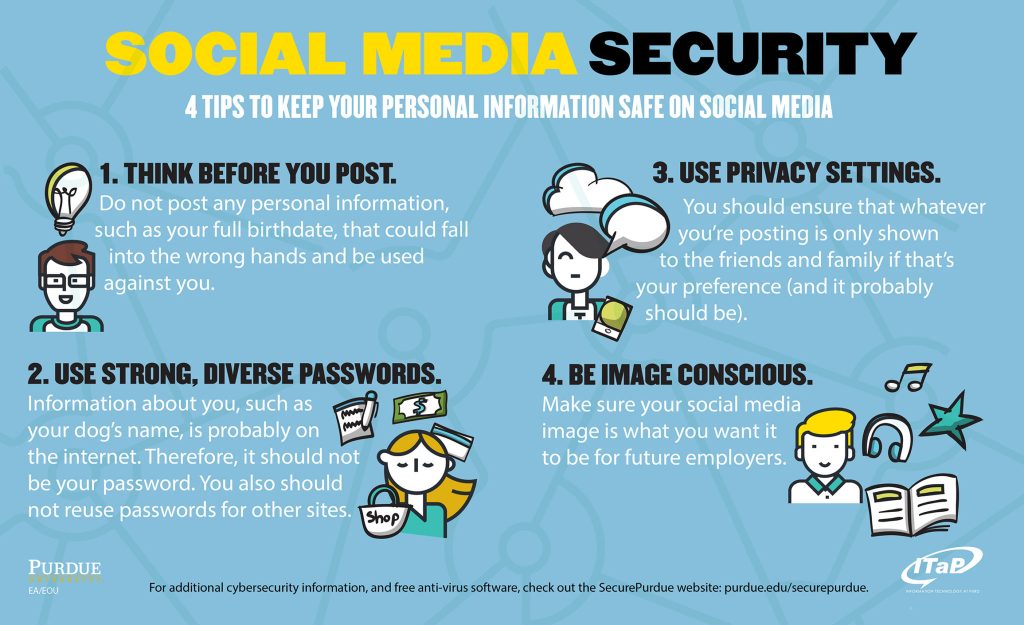
Thankfully, users of various social networking platforms are not alone in the fight to protect themselves. A majority of the social networking sites have configurable security settings for your account. Accounts can either be public or private. Switching one’s social media page to private will not disconnect you from your friends and family but instead prevent third parties from snooping on your information.
There is no denying that social networking has been adopted in the masses and will continue to do so. The benefits and opportunities that come with social networking are great but so is the importance of safe and responsible usage.
References:
[1] Miriam, J. “Books Are Social.” Books Are Social, 3 June 2019, http://www.booksaresocial.com/social-media-timeline-2019/.
[2] Chaffey, Dave. “Smart Insights.” Smart Insights, 7 Apr. 2020, https://www.smartinsights.com/social-media-marketing/social-media-strategy/new-global-social-media-research/.
[3] Tiwari, Aditya. “What Is Social Engineering? What Are Different Types Of Social Engineering Attacks?” Fossbytes, 30 May 2018, fossbytes.com/what-is-social-engineering-types-techniques/.
[4] “Purdue.edu.” Purdue.edu, Purdue University, 2017, https://www.purdue.edu/research/dimensions/infographic-social-media-security/.